This is another GitHub project introduction post. This time introduces a repo that shows how an end-to-end Azure solution can be set up from Azure DNS -> Public IP Address -> Azure App Gateway -> Azure Kubernetes Service with Application Gateway Ingress controller AGIC hereafter.
This is a standard use case of how to expose a web application from Kubernetes via standard Azure networking services such as DNS, Public IP Address and AAG
Problem
When we want to route traffic to AKS, the primary question is how to set up the ingress. Traditionally we use NGINX ingress controller and it was not a question at all. Now with Azure Application Gateway Ingress Controller, we just need to justify the decision.
What is Application Gateway Ingress Controller?
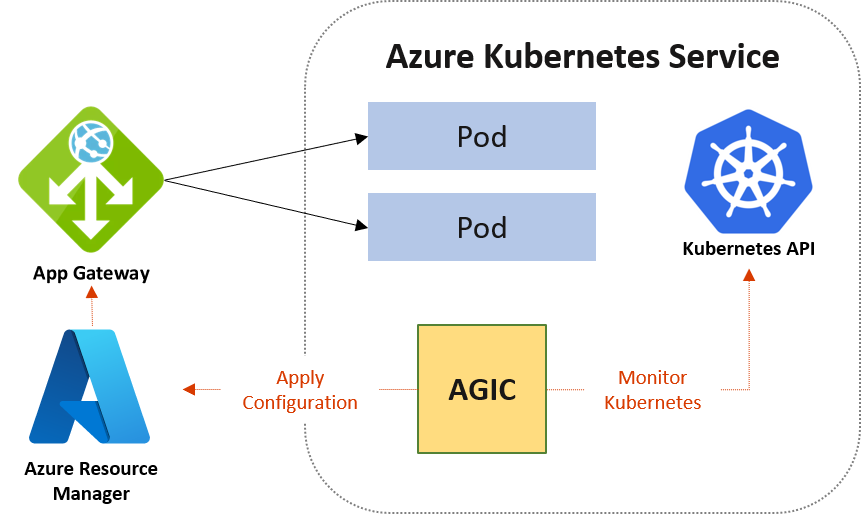
It is one of the Kubernetes Ingress controllers that can only work with Azure Application Gateway. The major differences with NGINX are
- AGIC will monitor the cluster and update the Azure Application Gateway back with routing IPs.
- AGIC uses Pod IPs as the backend instead of the service IP address. If there are 3 pods there will be 3 IPs in the Application Gateway backend pool
- In order to update the Azure App Gateway, the AGIC should have Azure RBAC permissions via user-assigned managed identity.
Photo credits go to the official docs.
My recommendation is not to use this AGIC as it's having issues.
There will be a separate post on issues with AGIC.
Setting up
Below is the repo that has biceps and required PowerShell to set up end to end.
Please note not all things are automated. Readme.md has the details.


No comments:
Post a Comment