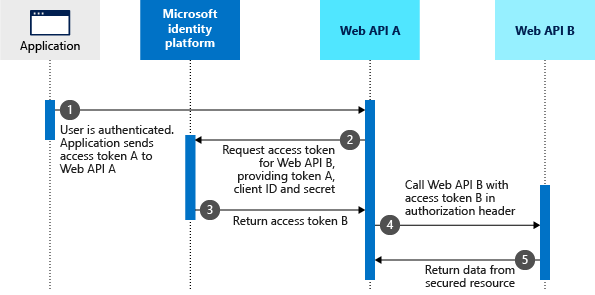
Often we encounter situation where we have one web api that needs to call another api as the incoming user. Basically our web api needs to impersonate the user to the next downstream api. Below goes the official diagram¹ from Microsoft.
Let us call the Web API A as middle tier API and Web API B as down stream api. Here we assume our application is an Angular web app.Coding that auth flow is little complex. Before coding it is always good to understand how this can be done using Postman.
This require setting up Azure app registrations which are tricky to many developers. So we will detail those out. A glance of sample setup is below
- Application
- App registration (aad-testapp/b34ade37-*)
- This app registration should have Postman's redirect url "https://oauth.pstmn.io/v1/callback"
- This needs to have secret to be used from Postman
- This should have permission to call aad-testapi1 with admin consent to avoid runtime individual user consent.
- Middle tier web api (Web API A)
- App registration (aad-testapi1/b6d5852b-*)
- This should have secret to be used while asking for ob behalf of token
- This should have permission to call aad-testapi2 with admin consernt to avoid runtime user consent.
- Downstream api (Web API B)
- App registration - (aad-testapi2/67d35db8-*)
- No need to have certificates or secrets as this is not getting any token.
- The expose and API section to have the aad-testapi1 to authorize and to avoid any consent
App registration for application (aad-testapp)
App registration for Middle tier api(aad-webapi1)
App registration for down stream api(aad-webapi2)
Getting First token A
Here below 3 fields may attract queries.
Let us details it, if the screenshot is not enough.
- Auth Url - The url that ends with /authorize.
- Access Token Url - The url that ends with /token.
These 2 urls can be seen if we take fiddler traces when the token is requested from Postman.
- Scope - the scope to the aad-webapi1.
Getting on behalf of token B
The url we are using is the normal token url of the tenant.
- grant_type - no idea why it needs to be this string. It is as per the docs³. We normally expect this to be 'on_behalf_of', but it is not.
- requested_token_use - here comes the word 'on_behalf_of'
- client_id - is the id of middle tier app registration
- client_secret - created in middle tier app registration
- scope - poining to downstream api
- assertion - this is the incoming token to middle tier api from the client application.
When we are coding in .Net we can use X509 certificate instead of client_secret
Reference
- ¹ - https://learn.microsoft.com/en-us/entra/identity-platform/v2-oauth2-on-behalf-of-flow#protocol-diagram
- ² - https://teamfolio.co.uk/blog/configure-postman-to-use-azure-active-directory-authorisation
- ³ - https://learn.microsoft.com/en-us/entra/identity-platform/v2-oauth2-on-behalf-of-flow#first-case-access-token-request-with-a-shared-secret












No comments:
Post a Comment